Protect Your
Computer: Must-Know Windows Security Tips for Every User
 |
| Protect Your Computer: Windows Security Tips for Every User |
|
Security is an essential feature of the contemporary world especially since our lives are highly digitalized. Be it identity details, monetary records or working papers, the protection of our information is very important. Since many populations use windows computers, such computers are usually prone to many security threats. To that end, in this blog, I will inform you of some important tips and practices that you need to follow if you are to secure your Windows PC optimally.
Understanding
the Basics of Computer Security:
It is pertinent to note basic Computer Security, before moving towards the various measures of security. Most of the users have a wrong opinion of protection and think that the purchase of antivirus software is enough. However, while antivirus software is extremely valuable and a must-have in your arsenal it constitutes merely a mere 10 percent of your security strategy. The rest of the ninety percent is self-implementation based on the best practice and the user behavior.
It is equally important to know what you should not do as it is to know the things that you can do to protect yourself. Having elaborated on the basics of Windows security setup and the supporting information let’s delve into the methods of protection.
Windows Security Tips for Every User
.webp) |
| Windows Security Tips for Every User |
Account Management: Choosing between a local and a Microsoft account:
A user account combined with a password is the first level of a barrier that any unauthorized personnel needs to overcome. Using the Windows 10, you are required to sign up with a local account or a Microsoft account. However, accounts with Microsoft bring some convenience by using the accounts across the devices, but, at the same time, they expose the users to potential danger. Local account on the other hand stores your data within a particular device thus minimizing exposure to likely hacks.
To manage your accounts click on the accounts tab in the setting section of the web application. Navigate
to Settings > Accounts. Here you can see your current account type, here you can change it as well. Some of the settings are best executed when you are using the standard user account rather than the administrator account. This setting provides rights to administer the system that can install or modify software or system settings making it secure.
Utilizing
User Account Control (UAC)
User Account Control (UAC) is just an important tool that requires permission every time changes you want to make in your computer happens. Despite the fact that some users consider the UAC feature as a mere nuisance and may even be incline to shut them down, it is dangerous to do so. Maintaining UAC enabled will assist the system in buoying the changes made in the system.
To change settings for UAC, in the search box click on start and type “UAC” then select User Account Control settings. For easy use of Windows and especially when you are not that much familiar with the code of the computer, I will recommend that UAC should be set at its default level mainly because, if you have specific reasons that would require you to make changes on your Windows, then you have no other choice than to turn on the UAC.
Password Management:
Passwords are necessary for securing your accounts but due to complexity of password, people often use bad password practices. While most recommend the use of complicated passwords, these bring about the vice of users writing their passwords in unsafe places. However, instead of such expressions it is advisable to use phrases or any words that are better not to explain as they are easier to memorize and very difficult to decipher.
For instance, an a phrase like
"Blue Socks At Midnight" is bound to be unique and easy to remember than a string of characters … It’s unadvisable to be using the same password for different accounts, more so your email and your financial accounts.
And to change the password, you can follow the path of Settings > Accounts > Sign-in options. Here you are also able to type in or change your password specific to the local account.
Physical
Security: Protecting Your Device:
Physical security is the biggest threat to any software security measure because the physical access to your computer is all that is required. This is an undesirable course of action since if a person gains physical access to your device, he or she may go round the security systems in place. Hence, protection of device physically should be a top priority.
File encryption tools could be used in the work with the sensitive information; pertaining to the full disk encryption tools, one of the best options is the BitLocker available for the Windows Pro series. But see the catch; if you forget the actual BitLocker password or if access to your Microsoft account gets blocked, then your data is gone for good. Always keep your recovery key safe if you ever use the BitLocker feature in your device.
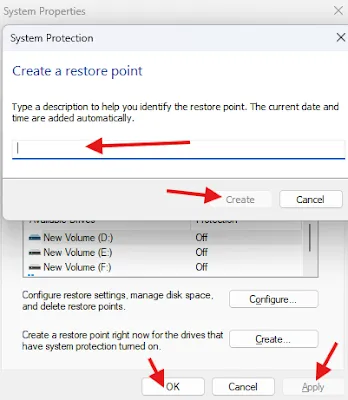
System Restore Points: A warmth insulating barrier of having a Safety Net:
 |
Create System Restore Points
|
|
The OS that practically all the computers come with is Win, and it has a built-in feature commonly referred to as System Restore which assists in the returning of the system to the previous state. Nonetheless, Microsoft has boot configuration deletion of restore point by default. Enabling this feature provides you with a security measure which restore your system in case there is a problem.
To set up
automatic creation of restore points follow the steps to navigate to "
Control panel", "
System and Security" and then click on
System followed by the "
System protection" link. From there go to select your drive and then by configuring the same you are able to turn on system protection. Restore points can also be set with a specific amount of disk space A restore point does therefore records the state of a predetermined amount of disk space or a particular disk at a specific time.
Antivirus Software: Last Line of Defense:
One thing to note is that antivirus, as effective as it is, is not the only security measure that should be employed but it nevertheless remains an extremely important element of your protection. Windows Security available in Windows 10 and 11 versions is quite effective without the need to buy more software. However, do make sure however it is up to date on anti-virus software.
Avoid third-party anti-virus programs, particularly the ones that need a subscription to be of service. Unfortunately, many of the users miss the notifications on subscription renewal hence their systems remain open to such attacks. Again the use of Windows Security is also effective and may be cheaper in the sense that it provides basic security.
Keeping Software Updated:
An up-to-date software is a necessity in the current world since it will help to enhance the security. Software authors often patch software’s for security purposes and for additional enhancements. Make sure that the ‘Windows Update’ facility is turned ON so as to enable the system to download important updates without your intervention.
Whereas feature update the user can delay, security updates should be applied at the earliest. Old system versions are still a target point for hackers, which is why these updates should not be delayed.
Using Secure DNS Servers:
The DNS
(Domain Name System) on your computer makes website names into a kind of "address." One may benefit from using a secure DNS server since it will alert him or her not to access the malicious sites. Precise services like the Google DNS or the OpenDNS offer additional operational security functions, for example, the blocking of the addresses of actual threats.
This section focuses on configuring DNS settings by; accessing the control panel, Then select network and internet, then select Network and sharing center, then select lastly change adapter settings. Here you should go to the start, right-click your Ethernet, choose properties and choose Internet Protocol Version 4 (TCP/IPv4). You can directly enter DNS server address that can be Google DNS address (8. 8. 8. 8 and 8. 8. 4. 4. )
Conclusion on security Practices:
In conclusion, good practices as well as favorable tools play crucial role in order to enhance security of your Windows PC. Most of the safety is derived from the knowledge of risks that might exist, and acting accordingly in a network environment. With the help of these tips and keeping updated with your security status, you’ve minimized the chances of losses and protected your information.
Do not forget that such a person who sits in front of a computer is one of the main pillars of security. Always do your own research as to what you as a business owner should be doing and remain cautious of possible dangers.
FAQs on Protecting Your Computer: Windows Security Tips
 |
| FAQs on Windows Security Tips |
General Security Tips:
- Keep Your System Updated: Newer versions of Windows need to be updated from time to time; this is mainly to install security updates.
- Strong Passwords: Choose strong and different passwords for your accounts and make sure that you change them on a regular basis.
- Beware of Phishing: Please be wary when someone sends you an email or sends you a message inquiring for personal data, you might be a victim of a phishing scam.
- Use Antivirus Software: Anti-virus should be installed and the software should be updated often and from a trustworthy source.
- Back Up Your Data: Make sure you copy your most vital documents on external hard drive or on cloud storage and update it on a consistent basis.
Specific Windows Security Measures:
- Windows Defender: Launch the Windows Defender, which is one of the effective free antivirus tools from the Windows Operating System.
- Firewall: Learn how to turn on and set up your Windows Firewall to ones whereby past access to networks is prohibited.
- User Account Control (UAC): Make sure you enable the User Account Control for it assists in notifying you before you make any changes that might affect your system adversely.
- Secure Boot: Enabling Secure Boot is optional but enhance the security of the system from launching a booting from an unauthorized software.
- BitLocker: Here it is possible to consider using BitLocker to encrypt hard drive and to protect information in case of computer loss or theft.
Online Security Best Practices:
- Secure Browsing: This can involve even using the correct web browser and not clicking on links or downloading files from untrusted source.
- Public Wi-Fi: It is not safe to engage in sensitive activities connected to the internet through the help of a public Wi-Fi because it is usually insecure.
- Online Shopping: When shopping online, only use secure link (https) and beware of the links that turns out to be phishing links.
- Two-Factor Authentication: Make sure to adjust your website accounts to propose the two-factor verification, which would make them more secure.
Remember: Just to know about all existing security threats and follow these best practices you can have a huge impact on your computer protection.

.webp)







1 Comments
Thank you so much for your feedback! I’m glad the content resonated with you. If you're interested in more insights, feel free to check out my website "Phone Stationary" where I share more tips and Trick. I appreciate your support and alignment with Webspacekit's mission!😊
ReplyDelete